Security guru Bruce Schneier warns about the lack of trust resulting from revelations about NSA domestic spying:
Both government agencies and corporations have cloaked themselves in so much secrecy that it's impossible to verify anything they say; revelation after revelation demonstrates that they've been lying to us regularly and tell the truth only when there's no alternative.
There's much more to come. Right now, the press has published only a tiny percentage of the documents Snowden took with him. And Snowden's files are only a tiny percentage of the number of secrets our government is keeping, awaiting the next whistle-blower.
Ronald Reagan once said "trust but verify." That works only if we can verify. In a world where everyone lies to us all the time, we have no choice but to trust blindly, and we have no reason to believe that anyone is worthy of blind trust. It's no wonder that most people are ignoring the story; it's just too much cognitive dissonance to try to cope with it.
Meanwhile, at the Wall Street Journal, Ted Koppel has an op-ed warning about our over-reactions to terrorism:
[O]nly 18 months [after 9/11], with the invasion of Iraq in 2003, ... the U.S. began to inflict upon itself a degree of damage that no external power could have achieved. Even bin Laden must have been astounded. He had, it has been reported, hoped that the U.S. would be drawn into a ground war in Afghanistan, that graveyard to so many foreign armies. But Iraq! In the end, the war left 4,500 American soldiers dead and 32,000 wounded. It cost well in excess of a trillion dollars—every penny of which was borrowed money.
Saddam was killed, it's true, and the world is a better place for it. What prior U.S. administrations understood, however, was Saddam's value as a regional counterweight to Iran. It is hard to look at Iraq today and find that the U.S. gained much for its sacrifices there. Nor, as we seek to untangle ourselves from Afghanistan, can U.S. achievements there be seen as much of a bargain for the price paid in blood and treasure.
At home, the U.S. has constructed an antiterrorism enterprise so immense, so costly and so inexorably interwoven with the defense establishment, police and intelligence agencies, communications systems, and with social media, travel networks and their attendant security apparatus, that the idea of downsizing, let alone disbanding such a construct, is an exercise in futility.
Do you feel safer now?
Our company needs a specific Microsoft account, not attached to a specific employee, to be the "Account Holder" for our Azure subscriptions.
Azure only allows one and only one account holder, you see, and more than one person needs access to the billing information for these accounts. Setting up a specific account for that purpose solves that problem.
So, I went ahead and set up an email account for our putative Azure administrator, and then went to the Live ID signup process. It asked me for my "birthdate." Figuring, what the hell?, I entered the birthdate of the company.
That got me here:
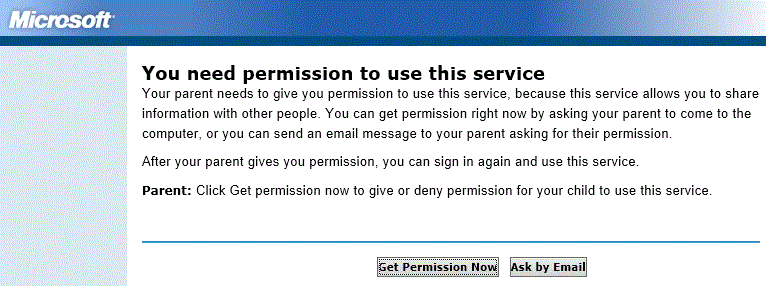
Annoying, but fine, I get why they do this.
So I got all the way through the process, including giving them a credit card to prove I'm real, and then I got this:

By the way, those screen-shots are from the third attempt, including one giving them a different credit card.
I have sent a message to Microsoft customer support, but haven't gotten an acknowledgement yet. I think I'm just going to cancel the account and start over.
Update: Yes, killing the account and starting over (by denying the email verification step) worked. So why couldn't the average pre-teen figure this out too? This has to be one of the dumber things companies do.
Security guru Bruce Schneier suggests Snowden might not have considered all the likely outcomes:
Edward Snowden has set up a dead man's switch. He's distributed encrypted copies of his document trove to various people, and has set up some sort of automatic system to distribute the key, should something happen to him.
Dead man's switches have a long history, both for safety (the machinery automatically stops if the operator's hand goes slack) and security reasons. WikiLeaks did the same thing with the State Department cables.
I'm not sure he's thought this through, though. I would be more worried that someone would kill me in order to get the documents released than I would be that someone would kill me to prevent the documents from being released. Any real-world situation involves multiple adversaries, and it's important to keep all of them in mind when designing a security system.
Possibly spending a few years at the Moscow airport might be his safest option. But then again, his whole strategy seemed flawed from the start.
I like keeping in touch with friends on Facebook. I also enjoy playing Scrabble. Soon-to-be-Internet-flameout Zynga has a Scrabble-like game called Words With Friends that many of my friends play. Right now I've got about 10 games going.
For the past week or so, Zynga has been shoving entire 30-second commercials between my turns. That is, I play a word, and I either spend the next 35 seconds or so with my computer muted and the Facebook window hidden, or I leave Words With Friends entirely. Since the advertisements all seem to be for cleaning products and—I kid you not—something to make my yeast infection go away, I'm leaving the game a lot more often.
Today I was finally annoyed enough to complain to Zynga on their player support page. It turns out, many, many people are complaining. Everyone seems to agree: we all understand that Zynga has to make some money, so we all understand we're going to see ads. But 30-second TV spots? After every move? No. That has to stop.
So here I was, about to post my own complaint, and I got this:
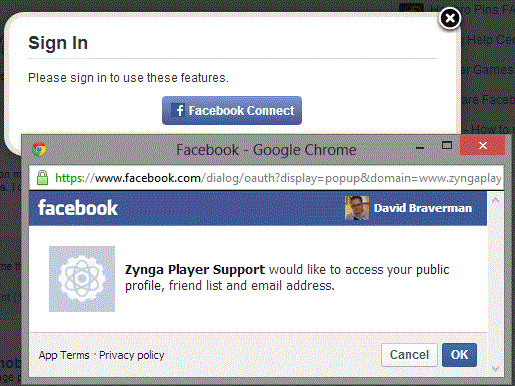
No, Zynga, you may not have access to my friends just so I can post a complaint. Anyway, you already have access to my friends through Facebook, because I had to consent to that to play the game—so why remind me?
Overnight, a commenter from Ireland took issue with my last post. I responded directly, but I thought my response might be worth repeating. I'm not sure I stated my point clearly enough: I wasn't actually discussing Snowden's leak; I'm saying we can't have an adult discussion about the leak any more, because he screwed up the end game.
The anonymous commenter wrote, inter alia:
Einstein fled. So did Hedy Lamar. So did thousands of others - including many who aided Germany's enemies. Were they cowards? Is the Dali Lama a coward?
It's interesting, I've just finished a history of inter-war Berlin, so I have some insight into Einstein's and Lamar's flights from Germany. The commenter essentially suggests that the U.S. has degenerated to the point where a plurality of voters are considering giving power to a group of armed thugs who have publicly and repeatedly announced plans to commit genocide.
Lamar, Einstein, the Dalai Lama—these people were persecuted for who they were, not for what they had done. Their departures from their home countries reflected their beliefs (correctly, it turns out) that their governments weren't worth preserving, that disobedience had no hope of changing anything, that they'd given up hope. Well, I haven't given up.
The commenter also pointed out:
Multiple nations collaborated to aid Snowden's journey. They did so in spite of huge amounts of US pressure. American soft power is an incredibly important thing if America wants to push her agenda - and this incident shows how damaged it is. Mass spying and deception has consequences.
Exactly right. And that's why I say Snowden scored an own goal.
We need to have an open and vociferous debate in the U.S. about the trade-offs between security and liberty, and Snowden could have done a lot to open up that discussion. Instead he ran, and that's all anyone will ever say about him. He conceded the argument on irrelevant grounds.
I agree that Manning and Schwartz deserved better. So did Mandela. But take a look at the example Ellsberg set. Snowden, if he'd been less narcissistic, might have done a lot of good for the country. It's really a shame.
Someday, when a far-future Gibson writes about this time in the American Republic, he'll have a paragraph about Edward Snowden. I've got a fantasy in which the future historian remarks on Snowden sounding the alarm against unprecedented government and private collusion against personal privacy, and how his leak sparked a re-evaluation of the relationships between convenience and security, and between government and industry.
But I've actually got a degree in history, and I can tell you that the future Gibson will probably write about how Snowden's cowardice gave those who crave security over liberty the greatest gift they could have gotten. (The same study of history, by the way, leads me to the conclusion that this happy circumstance really does come from Snowden and not from some shadowy conspiracy. Never mistake incompetence for malice.)
I don't have a lot to say, other than Snowden's flight to Venezuela by way of Russia and China allows the people who value security over liberty to claim that Snowden was an enemy of the state, so we shouldn't pay any attention to his message. Have American security services over-reached? Do we have less privacy than ever before? Does this give a future politician the tools to take the United States from a republic to a dictatorship? Yes to all three. But no one will be thinking about that any more.
For the record: I don't think we have any immediate worries. I don't know what the consequences of these disclosures will actually be; no one does. And I'm not scraping together all the gold I can find so I can make a midnight passage to Canada.
I am saying only this: Edward Snowden is an idiot. King went to jail. Mandela went to jail. Hell, Ellsberg was willing to go to jail, but he at least had the pulse of the public before stepping forward.
The thought has occurred to others, I'm sure: Snowden could have done a lot more good as a confidential source, or as a man of conviction, than he can do as a defector.
Oh, and Ed: good luck enjoying your freedom in Venezuela. There's a reason we have chilly relations with the Venezuelan government, and it's not entirely about oil.
After a lot of really difficult work and evaluating a half-dozen 3rd-party libraries, I've finally gotten a round-trip between a local ASP.NET application and SalesForce. This is the first victory in two big battles against the SalesForce integration model I've been fighting for the last two weeks.
The next hurdle will be to get the SalesForce API to accept my application's SAML assertion after the user is authenticated. I really have no idea how to do that yet—and no one I've spoken with knows, either.
Still, this was a good way to end a long work-week. And soon: pizza.
As a large part of my brain noodles on how to get multiple IDPs to work with a single RP, a smaller part of my brain has looked out the window and realized Chicago is having a normally crappy April:
- The are 5-13 after allowing a run in the bottom of the 13th last night in Milwaukee;
- It's
13°C 7°C and raining, which is great because we need the rain and cool weather; and
- ...well, that's all I got right now.
I had a third thing, but SAML got in the way, I guess.
...you know it's going to be bad. And it really is:
Passed in 2012 after a 60 Minutes report on insider trading practices in Congress, the STOCK Act banned members of Congress and senior executive and legislative branch officials from trading based on government knowledge. To give the ban teeth, the law directed that many of these officials' financial disclosure forms be posted online and their contents placed into public databases. However, in March, a report ordered by Congress found that airing this information on the Internet could put public servants and national security at risk. The report urged that the database, and the public disclosure for everyone but members of Congress and the highest-ranking executive branch officials -- measures that had never been implemented -- be thrown out.
The government sprang into action: last week, both chambers of Congress unanimously agreed to adopt the report's recommendations. Days later, Obama signed the changes into law.
Bluntest of all was Bruce Schneier, a leading security technologist and cryptographer. "They put them personally at risk by holding them accountable," Schneier said of the impact of disclosure rules on Congress members and DC staffers. "That's why they repealed it. The national security bit is bullshit you're supposed to repeat." (Three of the four experts we consulted opted for the same term of choice.)
As Schneier said, "There was a security risk, but it was not a national security risk. It was a personal Congressperson risk." And that was enough to stymie transparency.
One commenter on the original CRJ article points out, "Right, they're concerned about people getting their personal info online...as they pass CISPA."
This was a bipartisan effort, by the way.
Via Sullivan, a new Google Chrome plugin that allows you to embed secret messages in photos you post on Facebook:
That’s the idea behind Secretbook, a browser extension released this week by 21-year-old Oxford University computer science student and former Google intern Owen-Campbell Moore. With the extension, anyone — you, your sister, a terrorist — could share messages hidden in JPEG images uploaded to Facebook without the prying eyes of the company, the government or anyone else noticing or figuring out what the messages say. The only way to unlock them is through a password you create.
The extension is only available for the Google Chrome browser — Campbell-Moore cites its developer tools and popularity — and the messages are restricted to 140 characters. Less certain is what Facebook thinks; a spokesman declined to comment. But it’s still the first time anyone’s managed to figure out how to automate digital steganography — the practice of concealing messages inside computer files — through Facebook, the world’s biggest social media platform. Unlike cryptography, which uses ciphertext to encrypt messages, steganographic messages are simply hidden where no one would think to look.
Calling Bruce Schneier...