Canada has put the Prairie Provinces on a winter storm warning as "the worst blizzard in decades" descends upon Saskatchewan and Manitoba:
A winter storm watch is in effect for southern Manitoba and southeastern Saskatchewan, with snowfall accumulations of 30 to 50 centimetres expected mid-week, along with northerly wind gusts of up to 90 kilometres per hour, said Environment Canada on Monday.
“Do not plan to travel — this storm has the potential to be the worst blizzard in decades,” the agency warns.
The storm is expected to start Tuesday night, as a Colorado low pressure system moving toward Minnesota will bring a “heavy swath of snow” from southeastern Saskatchewan through most of southern Manitoba.
Snow will start to fall early in the evening near the U.S. border and move north overnight. Blowing snow and high winds will cause zero visibility and whiteout conditions, making driving treacherous.
Meanwhile, elsewhere:
And finally, prosecutors in Texas have declined to pursue charges against a 26-year-old woman arrested last week for infanticide after self-inducing an abortion. Welcome to the new 19th Century, at least in the religious South.
Via Molly White, a new company called Gripnr wants to monetize your D&D campaign, and it's as horrible as it sounds:
Gripnr plans to generate 10,000 random D&D player characters (PCs), assign a “rarity” to certain aspects of each (such as ancestry and class), and mint them as non-fungible tokens, or NFTs. Each NFT will include character stats and a randomly-generated portrait of the PC designed in a process overseen by Gripnr’s lead artist Justin Kamerer. Additional NFTs will be minted to represent weapons and equipment.
Next, Gripnr will build a system for recording game progress on the Polygon blockchain. Players will log into the system and will play an adventure under the supervision of a Gripnr-certified Game Master. After each game session is over, the outcome will be logged on-chain, putting data back onto each NFT via a new contract protocol that allows a single NFT to become a long record of the character’s progression. Gripnr will distribute the cryptocurrency OPAL to GMs and players as in-game capital. Any loot, weapons, or items garnered in-game will be minted as new sellable NFTs on OpenSea, a popular NFT-marketplace.
As a D&D veteran who once played a character (for 5 minutes) with Gary Gygax* as DM, I can't see how any gamer would want to do this. Molly White has spent the last two years documenting the ways scammers and grifters have used "the blockchain" and "NFTs" and other Web3 buzzwords to steal (or, as I believe, launder) billions of dollars. Gripnr seems like just one more scam, but I could be wrong: Gripnr could just be a lazy get-rich-quick scheme for its creators.
Now that I've got a few weeks without travel, performances*, or work conferences, I can go back to not having enough time to read all the news that interests me. Like these stories:
Finally, Michelin has handed out its 2022 stars for Chicago. Nothing surprising on the list, but I now have four more restaurants to try.
* Except that I volunteered to help a church choir do five Messiah choruses on Easter Sunday, so I've got two extra rehearsals and a service in the next 12 days.
Bonus update: the fog this morning made St Boniface Cemetery especially spooky-looking when Cassie and I went out for her morning walk:

Via Bruce Schneier, a developer who maintains one of the most important NPM packages in the world got pissed off at Russia recently, without perhaps thinking through the long-term consequences:
A developer has been caught adding malicious code to a popular open-source package that wiped files on computers located in Russia and Belarus as part of a protest that has enraged many users and raised concerns about the safety of free and open source software.
The application, node-ipc, adds remote interprocess communication and neural networking capabilities to other open source code libraries. As a dependency, node-ipc is automatically downloaded and incorporated into other libraries, including ones like Vue.js CLI, which has more than 1 million weekly downloads.
“At this point, a very clear abuse and a critical supply chain security incident will occur for any system on which this npm package will be called upon, if that matches a geolocation of either Russia or Belarus,” wrote Liran Tal, a researcher at Snyk, a security company that tracked the changes and published its findings on Wednesday.
“Snyk stands with Ukraine, and we’ve proactively acted to support the Ukrainian people during the ongoing crisis with donations and free service to developers worldwide, as well as taking action to cease business in Russia and Belarus,” Tal wrote. “That said, intentional abuse such as this undermines the global open source community and requires us to flag impacted versions of node-ipc as security vulnerabilities.”
Yeah, kids, don't do this. The good guys have to stay the good guys because it's hard to go back from being a bad guy.
In an authoritarian regime, telling your boss that he did something wrong can have fatal consequences. Therefore people avoid mentioning problems up the chain. Like, for example, that mandating the army use only Russian-made mobile phones, even though Western electronics have progressed years or decades beyond them, might leave the army at a disadvantage in combat. Similarly, as an engineer, you might not tell your superiors that blowing up the enemy's 3G cell towers will render your 3G phones unusable, even while the enemy gets along fine with 4G.
So by not wanting to risk your life or career by telling a general that his plan sucks, the general might wind up dead and you might wind up informing the world on an open channel, like these FSB guys did:
A Russian general has been killed in fighting around Kharkiv, Ukrainian intelligence has claimed, which would make him the second general the Russian army has lost in Ukraine in a week.
The investigative journalism agency Bellingcat said it had confirmed Gerasimov’s death with a Russian source. Its executive director, Christo Grozev, said they had also identified the senior FSB officer in the intercepted conversation.
“In the call, you hear the Ukraine-based FSB officer ask his boss if he can talk via the secure Era system. The boss says Era is not working,” [Bellingcat executive director Christo] Grozev said on Twitter. “Era is a super expensive cryptophone system that [Russia’s defence ministry] introduced in 2021 with great fanfare. It guaranteed [to] work ‘in all conditions’.”
Grozev's Twitter thread has a point of view, of course, but wow. It's almost like the Russian military wants to lose this war. "The Russian army is equipped with secure phones that can't work in areas where the Russian army operates," Grozev Tweeted.
I just started Sprint 52 in my day job, after working right up to the last possible minute yesterday to (unsuccessfully) finish one more story before ending Sprint 51. Then I went to a 3-hour movie that you absolutely must see.
Consequently a few things have backed up over at Inner Drive Technology World Headquarters.
Before I get into that, take a look at this:
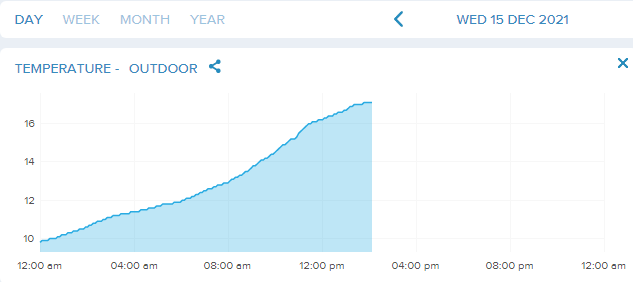
That 17.1°C reading at IDTWHQ comes in a shade lower than the official reading at O'Hare of 17.8°, which ties the record high maximum set in 1971. The forecast says it'll hang out here for a few hours before gale-force winds drive the temperature down to more seasonal levels overnight. I've even opened a few windows.
So what else is new?
So what really is new?
But Sprint 52 at my office, that's incredibly new, and I must go back to it.
Fed up with manufacturers releasing Internet-connected products for the home with inadequate security that puts everyone in the world at risk, the UK has finally cracked down:
Default passwords for internet-connected devices will be banned, and firms which do not comply will face huge fines.
The Product Security and Telecommunications Infrastructure Bill lays out three new rules:
- easy-to-guess default passwords preloaded on devices are banned. All products now need unique passwords that cannot be reset to factory default
- customers must be told when they buy a device the minimum time it will receive vital security updates and patches. If a product doesn't get either, that must also be disclosed
- security researchers will be given a public point of contact to point out flaws and bugs
The new regime will be overseen by a regulator, which will be appointed once the bill comes into force. It will have the power to fine companies up to £10m [$1.3m] or 4% of their global turnover, as well as up to £20,000 [$26,700] a day for ongoing contraventions.
About bloody time, I say. Yes, people should know better than to connect open Internet ports to their home networks, but most people in the world do not understand what any of that means. We don't make people mix their gasoline with air when driving anymore for the same reasons.
My 8am meeting with colleagues in London had to wait until 9:30 because Comcast screwed the pooch this morning:
Reports indicate the system was down, or at least unsteady, in areas stretching from Chicago to Philadelphia, New Jersey, and South Carolina. Looking at DownDetector, issues had been reported earlier in the Bay Area, but it’s unclear if those are connected to the problems people saw this morning.
Comcast has released a statement regarding the outage. According to a spokesperson, “Earlier, some customers experienced intermittent service disruptions as a result of a network issue. We have addressed the issue and service is now restoring for impacted customers, as we continue to investigate the root cause. We apologize to those who were affected.” It appears that most of the people who reported problems have confirmed they’re back online. There’s still no word on exactly what caused the problem or how many people were impacted at its peak.
In Chicago, the outage affected thousands of people from about 7:30 to 9, by which time I'd already relocated to my company's Loop office.
Oh, and on the day before a trip, my bank called to let me know their fraud department killed my primary credit card. They hope the new one arrives before I leave for the airport.
Yay.
I had to pause the really tricky refactoring I worked on yesterday because we discovered a new performance issue that obscured an old throttling issue. It took me most of the morning to find the performance bottleneck, but after removing it a process went from 270 seconds to 80. Then I started looking into getting the 80 down to, say, 0.8, and discovered that because we're using an API limit with a request limit (180 requests in 15 minutes), I put in a 5-second delay between requests.
Sigh.
So now I've got all this to read...someday:
Finally, the economics of workers vs employers has taken an odd turn as job applicants have started simply ghosting interviewers. But, as Slate says, "employers have been doing this to workers for years, and their hand-wringing didn’t start until the tables were turned."
Quick hit list of stuff I didn't find time to read:
Finally, Alexandra Petri guesses about the books that Republican candidate for Virginia Governor Glenn Youngkin might put on your kid's AP curriculum.